The following article shows how to integrate your Shodan Monitor with Azure Sentinel.
First of all, you will need an Azure Sentinel service associated with Log Analysis (Workspace ID/Key in Settings/ Agents Configuration are required for deployment). Follow here to install Azure Sentinel.
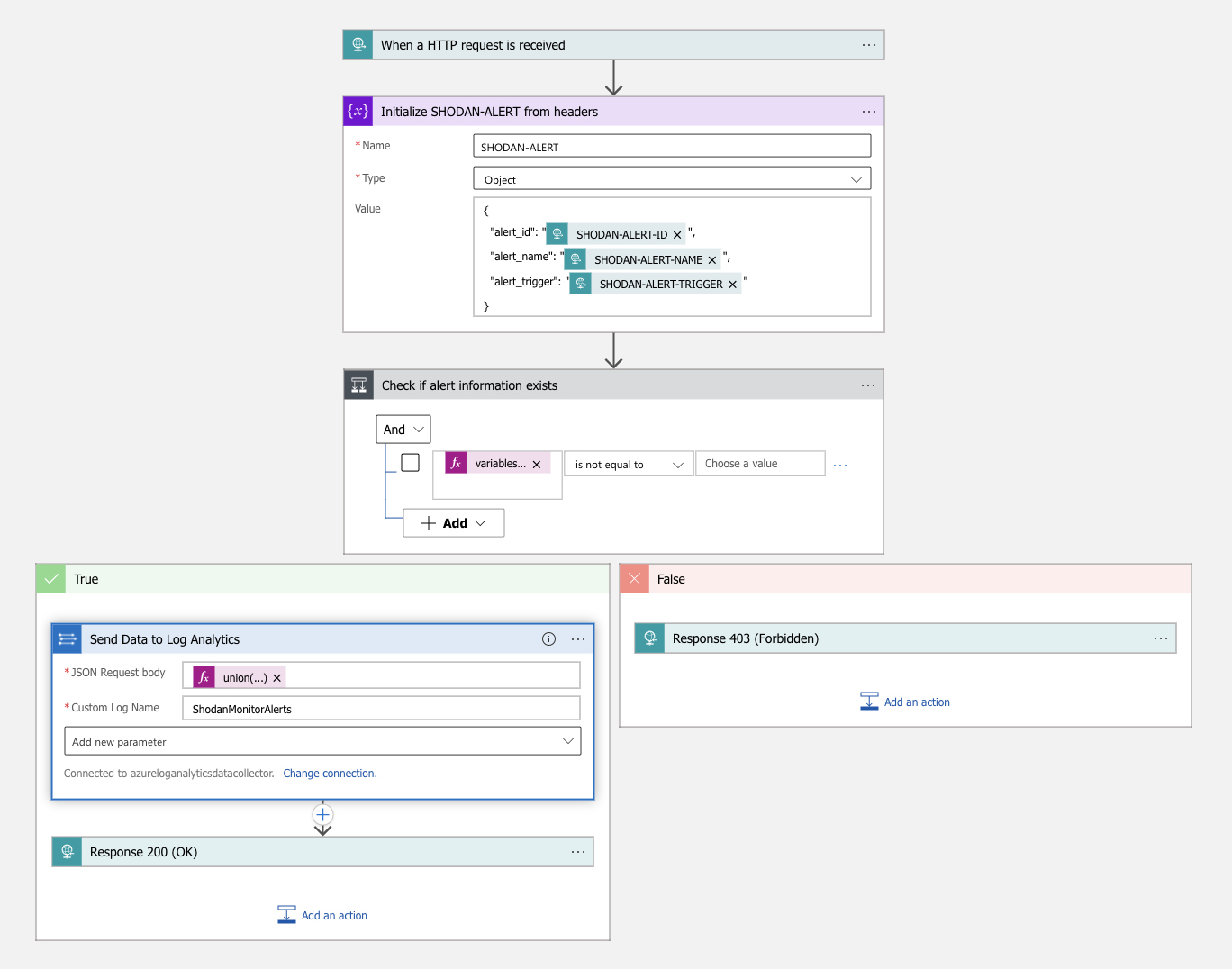
And then create a Logic App workflow which will trigger on HTTP received request, process it and send data to Sentinel. Click the deploy button below to instantly integrate it, what it does in summary:
Here is a visualization from Logic App designer:
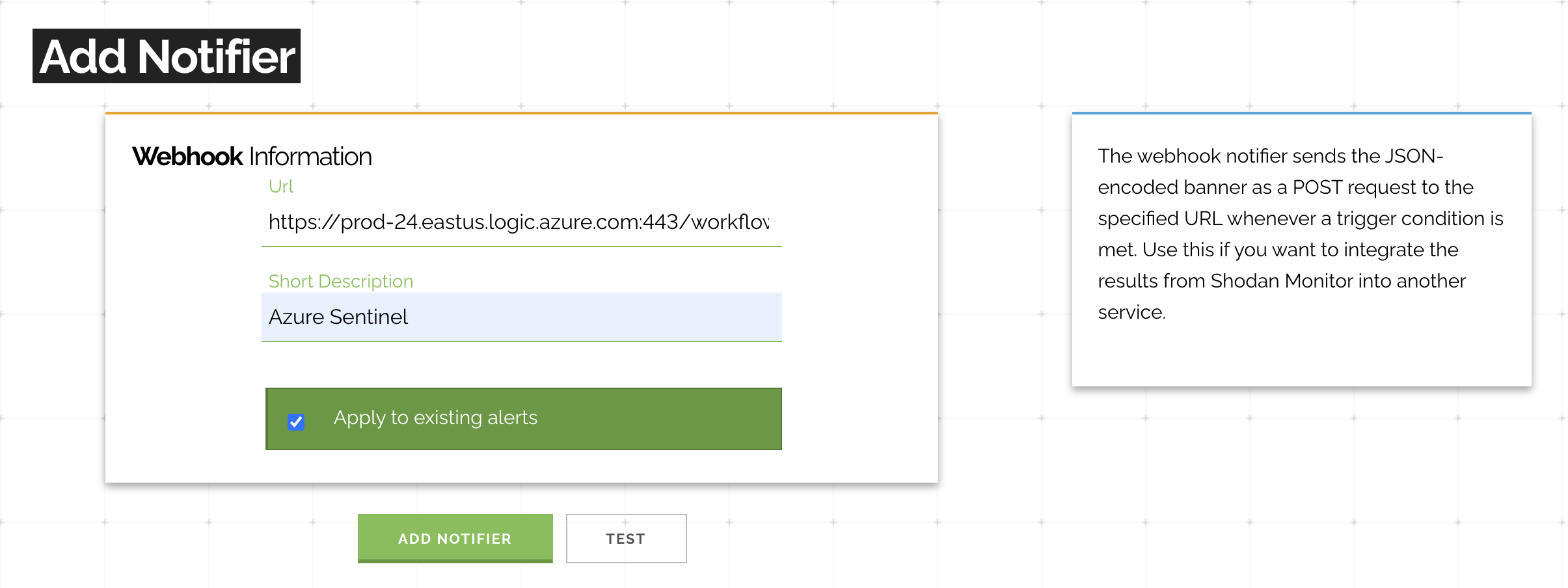
After successful deployment, copy the webhook URL and apply it to your existing alerts in Shodan Monitor.

Copy the above webhook URL into the Url field when creating a new webhook notifier:
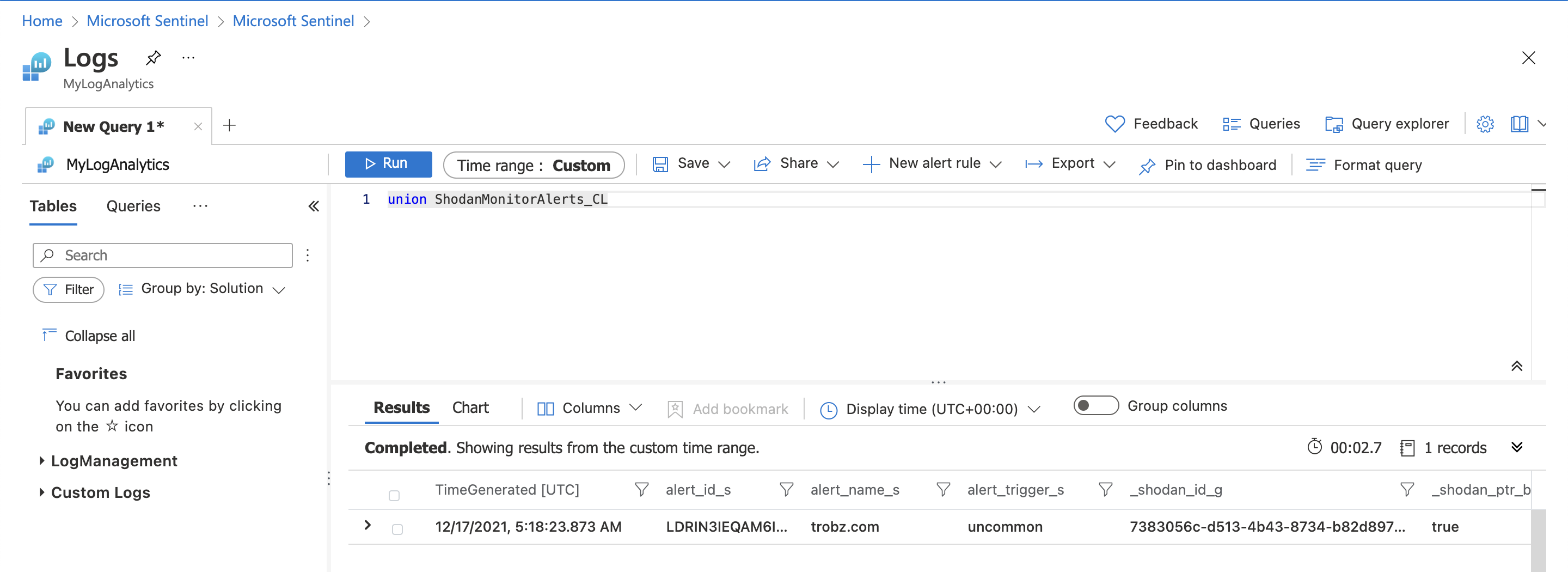
Once the configuration has been completed you will start seeing alerts within Azure Sentinel as Shodan crawls your networks:
Special thanks to Mikko Koivunen for creating the Azure deployment file and writing about it on his blog.