With Shodan it's easy to get an overview of the security for a country. Real-world borders don't necessarily translate to the Internet but it can still reveal useful information as shown by OECD. In this article we will use Shodan to get a big picture view of a country; in this case we're going to be looking at the USA.
First, lets have a look at how SSL is deployed in the USA. We will start off by getting a breakdown of the SSL versions that are supported by web servers using the Shodan CLI:
$ shodan stats --facets ssl.version country:US has_ssl:true HTTP
The ssl.version property contains a list of SSL versions that the web server supports and by faceting on that property we can get a distribution of supported SSL versions. This is possible because Shodan crawlers explicitly test for SSLv2 through TLSv1.2.
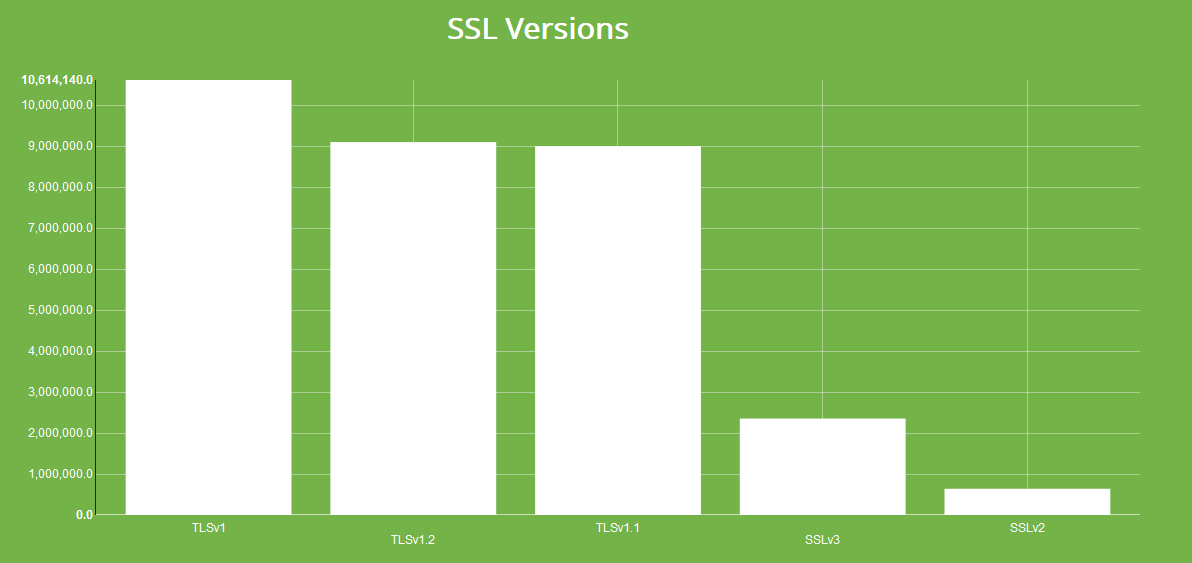
Unsurprisingly, the majority of the HTTPS servers are hosted by Akamai and Amazon. However, there's still a sizable chunk (600,000+) devices that support SSLv2 so lets look at those briefly:
$ shodan stats --facets org country:US ssl.version:sslv2 HTTP
Here I'm faceting on the org (organization) property and filtering for web servers that support SSLv2. This doesn't mean that they only accept SSLv2 connections but it is one of the versions the service supports.
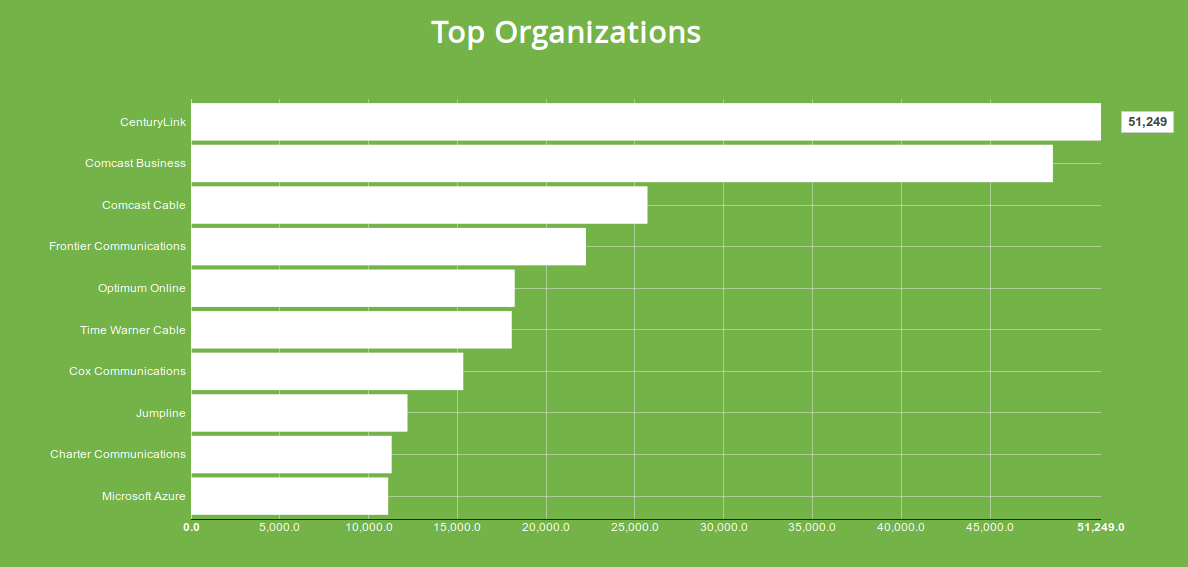
Around 10% of the services that support SSLv2 are operating on CenturyLink's network. Just looking at the results it seems like some of CenturyLink's modems are the reason for their #1 spot on the list. In general, would want to monitor these numbers over time to see whether CenturyLink is continuing to deploy these insecure modems over time or whether these are old devices that will be phased out. For this instance, we have been keeping track of these numbers using Shodan Reports and can say that CenturyLink has been slowly removing these insecure devices from their customers' networks.
The Shodan crawlers also check for the various SSL vulnerabilities such as Heartbleed and FREAK so lets see how the US fares for those. For Heartbleed there are at least ~34,000 devices in the US still vulnerable to it.
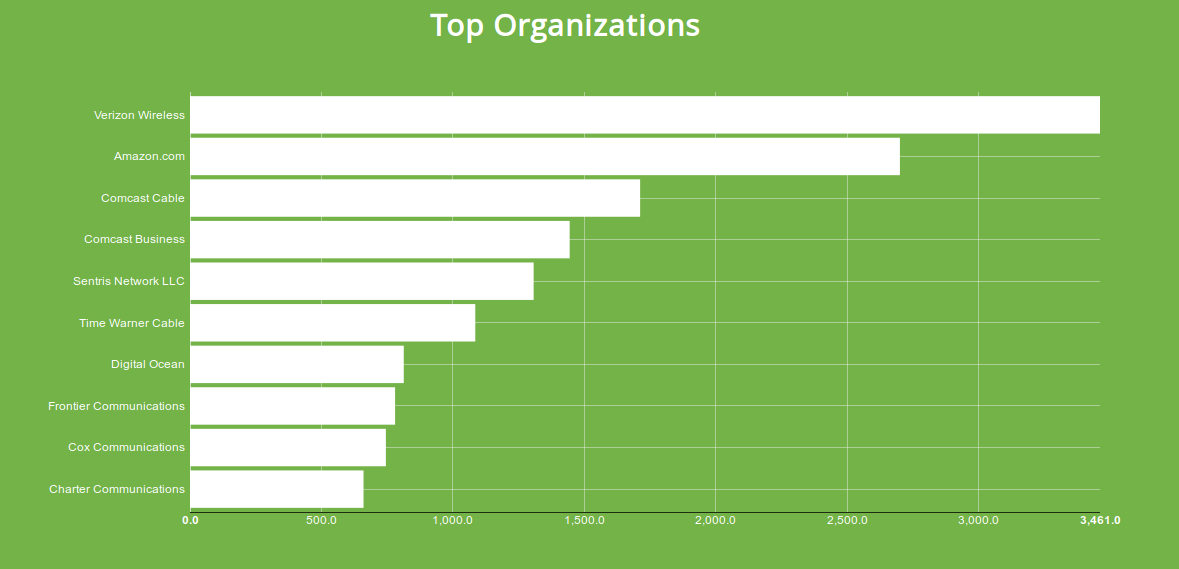
Interestingly, Verizon Wireless is the network with the most services vulnerable to Heartbleed. The runner-up, Amazon, is less surprising since it's not unusual for people to deploy old images that haven't yet been patched (or lack protection). There are 2 types of devices operated by Verizon Wireless that are affected:
Wireless routers that run on the alternate HTTPS port 8443 and are made by CradlePoint Technology.
Digital billboards made by Watchfire Signs that run a web server on port 9443.
These observations make sense in the context that we wouldn't expect to see many regular web servers on a mobile network such as Verizon Wireless. However, it's extremely common to see various embedded systems on these sorts of networks. The same analysis can be performed by looking at services that support export ciphers (CVE-2015-0204) as well as Ticketbleed (CVE-2016-9244) which I will leave as an exercise.
Finally, lets look at the distribution of SSL certificates. It usually isn't a good sign if the same SSL certificate is deployed across a large number of devices. To see the usage of duplicate SSL certificates we can facet on the ssl.cert.fingerprint property:
$ shodan stats --facets ssl.cert.fingerprint country:us has_ssl:true http
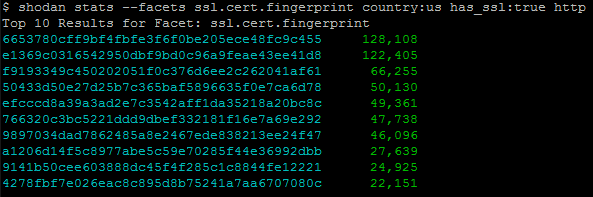
The results of the command will give us the 10 most common SSL certificate fingerprints:
If you want to get more than 10 you can also provide a number to the facet. For example, this is how to get the top 100 SSL fingerprints:
$ shodan stats --facets ssl.cert.fingerprint:100 country:us has_ssl:true http
The most common SSL certificate is for what looks like Google's CDN on IPv6. However, the 2nd most often seen SSL certificate is for Ecommerce Corporation which is a familiar company if you've read the article on Tracking Hacked Websites.
Here is a short video that shows how a similar analysis performed for Germany:
SSL is only one of many aspects that should be looked at and that Shodan collects information on. The same sort of techniques used in this article can be applied to other services/ devices such as SMB or industrial control systems. Review the documentation on available filters and facets for direction on how to investigate the types of services you care about.